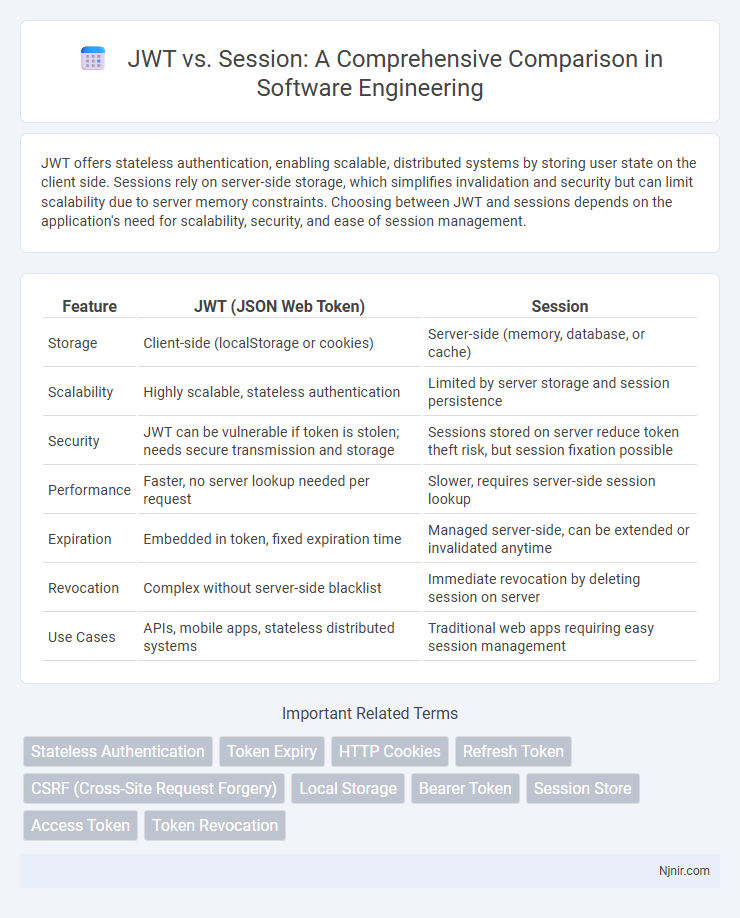
JWT offers stateless authentication, enabling scalable, distributed systems by storing user state on the client side. Sessions rely on server-side storage, which simplifies invalidation and security but can limit scalability due to server memory constraints. Choosing between JWT and sessions depends on the application's need for scalability, security, and ease of session management.
Table of Comparison
| Feature | JWT (JSON Web Token) | Session |
|---|---|---|
| Storage | Client-side (localStorage or cookies) | Server-side (memory, database, or cache) |
| Scalability | Highly scalable, stateless authentication | Limited by server storage and session persistence |
| Security | JWT can be vulnerable if token is stolen; needs secure transmission and storage | Sessions stored on server reduce token theft risk, but session fixation possible |
| Performance | Faster, no server lookup needed per request | Slower, requires server-side session lookup |
| Expiration | Embedded in token, fixed expiration time | Managed server-side, can be extended or invalidated anytime |
| Revocation | Complex without server-side blacklist | Immediate revocation by deleting session on server |
| Use Cases | APIs, mobile apps, stateless distributed systems | Traditional web apps requiring easy session management |
Introduction to JWT and Session Authentication
JSON Web Tokens (JWT) are a compact, URL-safe means of representing claims between two parties, commonly used for stateless authentication by encoding user information and expiration details within the token itself. Session authentication relies on server-side storage where user information is maintained on the server, and a session ID is stored as a cookie in the client's browser to track authenticated users. While JWT enables scalability through reduced server load by avoiding server-side storage, session authentication provides control and immediate invalidation by managing state directly on the server.
How JWT Works in Modern Applications
JWT (JSON Web Token) operates by encoding user information and claims into a digitally signed token transmitted between client and server, enabling stateless authentication without server-side session storage. The client sends the JWT in the Authorization header with each request, allowing the server to verify the token's signature and user identity quickly, enhancing scalability and performance in modern applications. JWTs support distributed systems by eliminating the need for centralized session management, making them ideal for microservices and single-page applications.
Session-Based Authentication Explained
Session-based authentication stores user credentials and session data on the server, creating a unique session ID that is sent to the client as a cookie. This session ID links the client to server-side stored information, enabling secure, stateful user authentication across multiple requests. Unlike JWT, which is stateless and self-contained, session-based authentication relies heavily on server memory and session storage management for tracking active user sessions.
Key Differences Between JWT and Session
JWT (JSON Web Token) stores user authentication data on the client side as a signed token, enabling stateless, scalable server designs, while Sessions store data on the server side with a unique session ID maintained in a client cookie, ensuring tighter control over user state. JWT's self-contained tokens reduce server memory usage but increase exposure risk if tokens are stolen, whereas Sessions offer immediate invalidation through server storage but require server overhead and state management. Security, scalability, token management, and storage location represent key differences critical to choosing between JWT and Session for authentication mechanisms.
Security Implications: JWT vs Session
JWT (JSON Web Tokens) store authentication data client-side, increasing exposure to token theft and replay attacks if not properly secured with HTTPS and short expiration times. Session-based authentication stores user state server-side, reducing risks from token interception but requiring secure management of session IDs and protection against session fixation and cross-site request forgery (CSRF). Implementing robust token invalidation and secure cookie attributes (HttpOnly, Secure, SameSite) enhances security for both JWT and session-based methods.
Scalability Concerns with JWT and Session
JWTs enable stateless authentication by embedding user data within the token, reducing server-side memory usage and enhancing scalability across distributed systems. Sessions require server-side storage, leading to increased memory consumption and complexity when scaling horizontally, especially in load-balanced environments. However, JWTs can introduce challenges with token revocation and size limitations, which must be carefully managed to maintain performance and security in large-scale applications.
Performance Comparison: JWT vs Session
JWT offers better scalability and reduced server load by storing user authentication data client-side, minimizing server memory usage during high traffic. Session-based authentication demands server memory for storing session data, which can lead to slower response times and increased server resource consumption under large user loads. Performance tests show JWT reduces latency in distributed systems by eliminating the need for frequent session store lookups, enhancing overall application responsiveness.
Use Cases and Best Practices
JWT (JSON Web Tokens) are ideal for stateless authentication in scalable APIs and single-page applications, enabling decentralized verification without server-side session storage. Sessions work best in traditional web applications requiring server-managed user state, providing enhanced control over session expiration and invalidation. For security, JWTs should include short expiration times and secure storage, while session management benefits from HTTPS enforcement and server-side session invalidation upon logout or suspicious activity.
Common Pitfalls to Avoid
Storing sensitive data directly in JWT payloads exposes risks of token leakage and potential security breaches; always keep tokens minimal and validate them on the server. Sessions often face issues with scaling in distributed systems, so implement centralized session stores like Redis to maintain consistency. Failing to set proper token expiration or secure cookie flags can lead to unauthorized access, making token management and secure storage critical for both JWT and session approaches.
Conclusion: Choosing the Right Authentication Method
Choosing between JWT and session-based authentication depends on the application's scalability, security requirements, and client architecture. JWT offers stateless, decentralized authentication ideal for microservices and mobile apps, while session-based authentication provides centralized control and is better suited for traditional web apps with server-side rendering. Evaluating factors like token storage, expiration handling, and server load ensures selecting the most efficient and secure method tailored to specific project needs.
Stateless Authentication
JWT enables stateless authentication by embedding user information within a signed token, eliminating the need for server-side session storage required in traditional session-based authentication.
Token Expiry
JWT tokens typically include an embedded expiration time that automatically invalidates the token after expiry, whereas sessions rely on server-side timeout settings to manage session expiration and user authentication validity.
HTTP Cookies
JWT stored in HTTP cookies enables stateless authentication with scalability, while sessions rely on server-stored data linked via cookies, affecting performance and security.
Refresh Token
Refresh tokens in JWT-based authentication enable secure, stateless token renewal without storing session data on the server, contrasting with traditional session management that relies on server-side session storage.
CSRF (Cross-Site Request Forgery)
JWT tokens stored in local storage are more vulnerable to CSRF attacks compared to session cookies with SameSite flags, which provide stronger CSRF protection.
Local Storage
JWT stored in Local Storage enables stateless authentication by securely maintaining tokens on the client side, while session-based authentication relies on server-side state management and cookies.
Bearer Token
Bearer tokens in JWT enable stateless authentication by securely transmitting user claims, whereas traditional session-based methods store session data server-side, impacting scalability and performance.
Session Store
Session stores in traditional session management securely maintain user state on the server side, enabling efficient session persistence and centralized control compared to stateless JWT authentication.
Access Token
JWT access tokens provide stateless, scalable authentication by securely encoding user data and expiration, unlike server-stored session tokens that require persistent session management.
Token Revocation
Token revocation in JWT systems requires additional mechanisms like blacklists or short expiration times, whereas session-based authentication allows immediate server-side invalidation by destroying the session.
JWT vs Session Infographic
 njnir.com
njnir.com