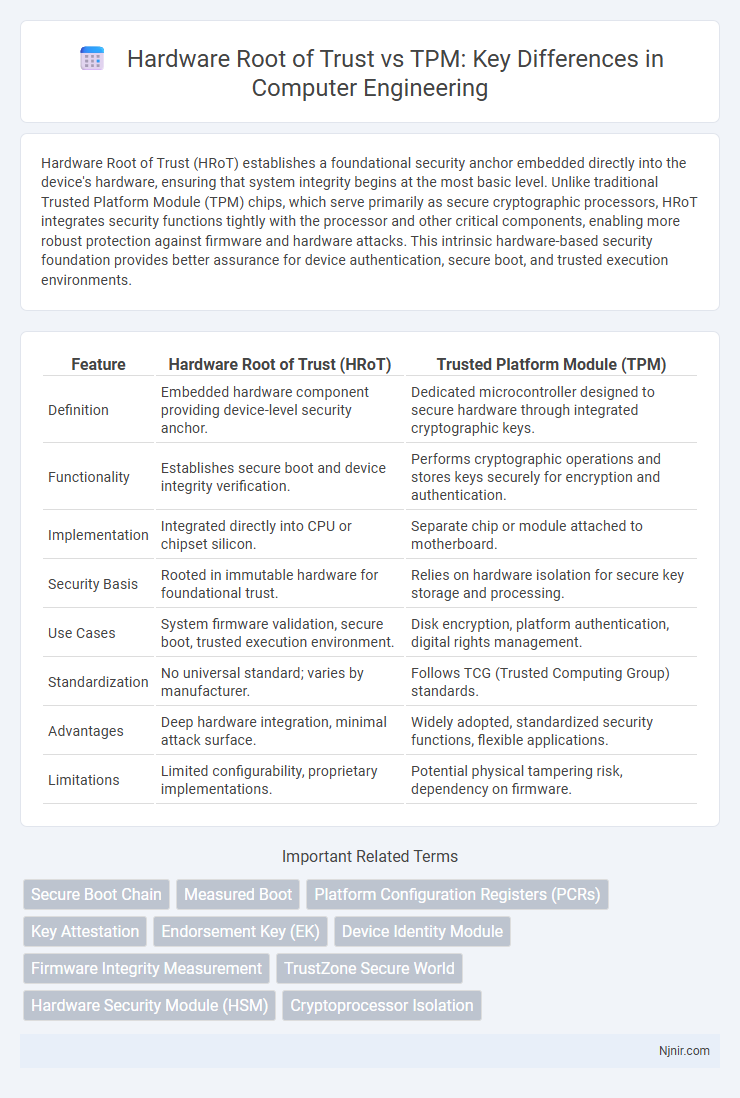
Hardware Root of Trust (HRoT) establishes a foundational security anchor embedded directly into the device's hardware, ensuring that system integrity begins at the most basic level. Unlike traditional Trusted Platform Module (TPM) chips, which serve primarily as secure cryptographic processors, HRoT integrates security functions tightly with the processor and other critical components, enabling more robust protection against firmware and hardware attacks. This intrinsic hardware-based security foundation provides better assurance for device authentication, secure boot, and trusted execution environments.
Table of Comparison
| Feature | Hardware Root of Trust (HRoT) | Trusted Platform Module (TPM) |
|---|---|---|
| Definition | Embedded hardware component providing device-level security anchor. | Dedicated microcontroller designed to secure hardware through integrated cryptographic keys. |
| Functionality | Establishes secure boot and device integrity verification. | Performs cryptographic operations and stores keys securely for encryption and authentication. |
| Implementation | Integrated directly into CPU or chipset silicon. | Separate chip or module attached to motherboard. |
| Security Basis | Rooted in immutable hardware for foundational trust. | Relies on hardware isolation for secure key storage and processing. |
| Use Cases | System firmware validation, secure boot, trusted execution environment. | Disk encryption, platform authentication, digital rights management. |
| Standardization | No universal standard; varies by manufacturer. | Follows TCG (Trusted Computing Group) standards. |
| Advantages | Deep hardware integration, minimal attack surface. | Widely adopted, standardized security functions, flexible applications. |
| Limitations | Limited configurability, proprietary implementations. | Potential physical tampering risk, dependency on firmware. |
Introduction to Hardware Root of Trust
Hardware Root of Trust (RoT) serves as the foundational security element embedded in a device's hardware, ensuring secure boot processes, cryptographic operations, and hardware-based authentication. Unlike a Trusted Platform Module (TPM), which is a specific hardware security chip designed to manage cryptographic keys and platform integrity, the Hardware RoT is a broader concept that can encompass various hardware components, including TPMs, secure enclaves, and cryptographic processors. This fundamental trust anchor establishes a chain of trust from the silicon level, enabling secure firmware loading and protection against unauthorized access or tampering.
Exploring the Trusted Platform Module (TPM)
The Trusted Platform Module (TPM) serves as a hardware root of trust by providing a secure cryptoprocessor designed to protect sensitive data through cryptographic keys and integrity measurements. TPM enables system integrity verification by securely storing platform measurements, which ensures trusted boot processes and attestation capabilities. Its integration within the hardware supports robust device security, safeguarding encryption keys, digital certificates, and authentication credentials against tampering and unauthorized access.
Core Functions of Hardware Roots of Trust
Hardware Roots of Trust establish a secure foundation by providing immutable, hardware-embedded cryptographic functions such as secure key storage, device identity, and cryptographic operations necessary for system integrity. Unlike the TPM, which serves as a discrete security chip with specific standardized functions like secure boot and attestation, Hardware Roots of Trust can be integrated directly into the main processor or SoC, enabling core security functions including secure boot, measured boot, and device authentication at the silicon level. Their core purpose centers on ensuring trustworthiness from the hardware level, facilitating secure boot processes, cryptographic key generation, and protection against firmware and software tampering.
TPM Architecture and Capabilities
The Hardware Root of Trust (HRoT) serves as the foundational security anchor in computing systems, ensuring integrity from the moment of boot. Trusted Platform Module (TPM) architecture is built on this principle, featuring dedicated cryptographic processors for secure key storage, platform integrity measurement, and attestation capabilities. TPMs provide robust functions such as secure generation and storage of cryptographic keys, platform integrity verification through PCRs (Platform Configuration Registers), and support for secure boot processes, enabling trusted computing environments essential for modern cybersecurity frameworks.
Security Standards: Hardware Root of Trust vs TPM
Hardware Root of Trust (RoT) establishes a foundational security anchor within a device by embedding immutable cryptographic keys and secure boot mechanisms directly into hardware. Trusted Platform Module (TPM) is a standardized hardware component that provides secure generation, storage, and management of cryptographic keys following security standards such as ISO/IEC 11889 TPM specification. While RoT serves as the fundamental security base, TPM enhances this trust by delivering certified hardware-based cryptographic functions compliant with industry-recognized security standards like FIPS 140-2 and Common Criteria.
Implementation in Computer Systems
Hardware Root of Trust (RoT) is a foundational security component embedded directly into a device's processor or chipset, ensuring a secure boot process by verifying firmware integrity at startup. Trusted Platform Module (TPM) is a specialized hardware chip designed to securely generate, store, and manage cryptographic keys, enhancing system authentication and encryption capabilities. While both RoT and TPM contribute to system security, RoT provides a minimal, immutable trust anchor for system integrity, whereas TPM offers broader cryptographic functions and persistent secure storage within computer systems.
Performance and Overhead Comparison
Hardware root of trust (RoT) offers lower overhead by integrating security functions directly into the silicon, resulting in faster cryptographic operations compared to TPM chips, which add additional latency due to separate hardware communication. TPM modules typically consume more power and introduce measurable delays during boot and attestation processes because they operate as discrete components. Performance benchmarks show hardware RoT can achieve cryptographic tasks in microseconds, whereas TPMs often take milliseconds, making hardware RoT more efficient for time-sensitive security workloads.
Real-World Use Cases and Applications
Hardware root of trust (RoT) provides a foundational security anchor embedded directly into devices, ensuring cryptographic keys and processes are protected against tampering. Trusted Platform Module (TPM) is a specialized RoT implementation widely adopted in PCs and enterprise servers to secure boot processes, encryption keys, and platform integrity verification. Real-world applications include secure firmware updates in IoT devices, trusted boot in laptops to prevent malware, and hardware-backed encryption in cloud infrastructure to protect sensitive customer data.
Vulnerabilities and Attack Resistance
Hardware root of trust (HRoT) provides foundational security by embedding cryptographic keys directly into silicon, offering robust protection against physical tampering but remains vulnerable to side-channel attacks and hardware fault injections. Trusted Platform Module (TPM), although also hardware-based, incorporates standardized cryptographic functions and secure storage, yet software vulnerabilities and firmware bugs can expose TPMs to sophisticated exploitation techniques like firmware rollback or privilege escalation. The attack resistance of HRoT exceeds TPM in hardware-level security assurance, but TPM benefits from wider industry adoption and ongoing software patches that mitigate emerging vulnerabilities over time.
Choosing Between Hardware Root of Trust and TPM
Choosing between Hardware Root of Trust (HRoT) and Trusted Platform Module (TPM) depends on the security requirements and device architecture of a system. HRoT provides a foundational, immutable security anchor integrated directly into hardware, enabling early-stage device validation and secure boot processes. TPM offers a standardized, discrete cryptographic module for key management, attestation, and secure storage, making it ideal for platforms requiring centralized and versatile security functions.
Secure Boot Chain
Hardware root of trust provides a foundational security anchor embedded in silicon for the Secure Boot Chain, while TPM (Trusted Platform Module) extends this trust by securely storing cryptographic keys and verifying platform integrity during boot.
Measured Boot
Hardware root of trust establishes a foundational security anchor in the device, enabling TPM to securely store cryptographic keys and perform Measured Boot by verifying firmware and software integrity at each startup step.
Platform Configuration Registers (PCRs)
Hardware root of trust leverages immutable Platform Configuration Registers (PCRs) to securely measure and store system state hashes, whereas TPM uses these PCRs within a standardized microcontroller to enable trusted boot and attestation processes.
Key Attestation
Hardware Root of Trust provides foundational security anchors for key attestation, while TPM (Trusted Platform Module) implements secure hardware-based key generation, storage, and attestation processes to verify device integrity and authentication.
Endorsement Key (EK)
The Endorsement Key (EK) in a TPM is a unique, hardware-rooted asymmetric key embedded during manufacturing, serving as a foundational trust anchor distinct from generic hardware roots of trust lacking such standardized cryptographic identity.
Device Identity Module
The Device Identity Module embedded in Hardware Root of Trust ensures secure device authentication and cryptographic key protection, offering stronger tamper-resistant identity verification compared to traditional TPM implementations.
Firmware Integrity Measurement
Hardware root of trust provides a foundational security anchor through immutable hardware-based keys, enabling trusted firmware integrity measurement, while TPM offers a standardized microcontroller-based solution for securely storing measurements and performing cryptographic operations to verify firmware authenticity.
TrustZone Secure World
TrustZone Secure World provides hardware root of trust by isolating secure execution environments at the processor level, whereas TPM offers dedicated cryptographic hardware for device authentication and integrity verification.
Hardware Security Module (HSM)
Hardware Security Modules (HSMs) provide a more robust hardware root of trust compared to TPMs by offering dedicated cryptographic key management, tamper-resistant protection, and scalable security functions for enterprise-grade applications.
Cryptoprocessor Isolation
Hardware Root of Trust ensures cryptoprocessor isolation by embedding immutable security functions directly into silicon, whereas TPM relies on a discrete cryptoprocessor module to provide isolated cryptographic operations.
Hardware root of trust vs TPM Infographic
 njnir.com
njnir.com