Transport Layer Security (TLS) is the modern, more secure protocol designed to replace Secure Sockets Layer (SSL) for encrypting data transmitted over networks. TLS provides enhanced encryption algorithms, improved handshake mechanisms, and stronger message authentication compared to SSL, reducing vulnerabilities to cyberattacks. Despite SSL being deprecated due to its security flaws, many legacy systems still use it, emphasizing the importance of migrating to TLS for robust data protection in computer engineering.
Table of Comparison
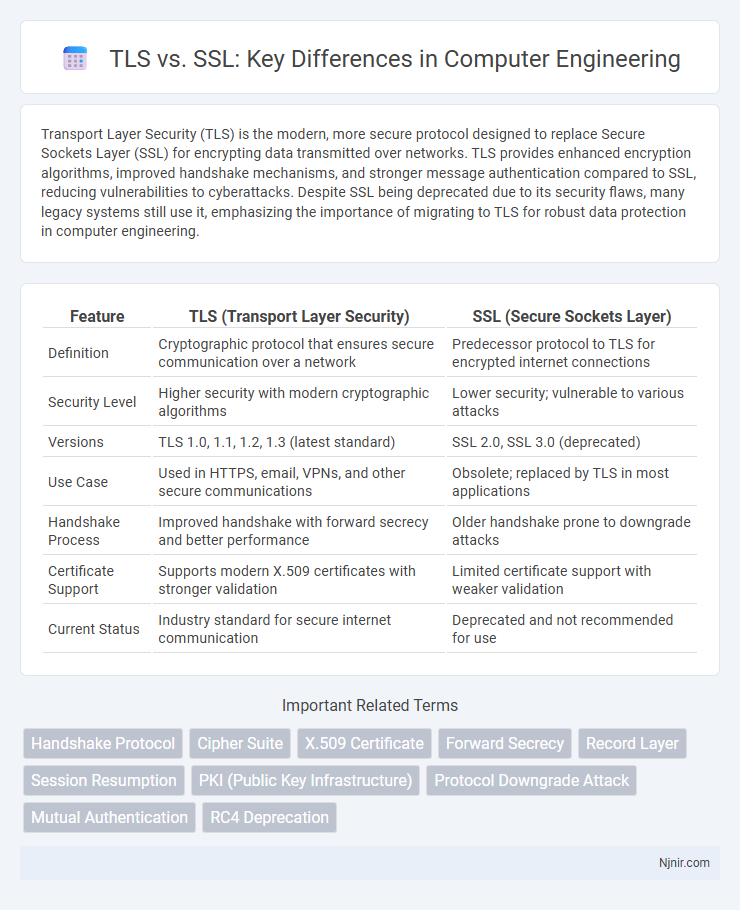
| Feature | TLS (Transport Layer Security) | SSL (Secure Sockets Layer) |
|---|---|---|
| Definition | Cryptographic protocol that ensures secure communication over a network | Predecessor protocol to TLS for encrypted internet connections |
| Security Level | Higher security with modern cryptographic algorithms | Lower security; vulnerable to various attacks |
| Versions | TLS 1.0, 1.1, 1.2, 1.3 (latest standard) | SSL 2.0, SSL 3.0 (deprecated) |
| Use Case | Used in HTTPS, email, VPNs, and other secure communications | Obsolete; replaced by TLS in most applications |
| Handshake Process | Improved handshake with forward secrecy and better performance | Older handshake prone to downgrade attacks |
| Certificate Support | Supports modern X.509 certificates with stronger validation | Limited certificate support with weaker validation |
| Current Status | Industry standard for secure internet communication | Deprecated and not recommended for use |
Introduction to TLS and SSL
TLS (Transport Layer Security) and SSL (Secure Sockets Layer) are cryptographic protocols designed to secure data transmitted over networks by providing encryption, authentication, and data integrity. SSL, developed by Netscape in the 1990s, served as the foundation for TLS, which is the more secure and modern protocol used today. TLS enhances SSL by addressing vulnerabilities and supporting stronger encryption algorithms, making it the standard for protecting internet communications such as HTTPS, email, and VPN connections.
Historical Evolution: From SSL to TLS
SSL (Secure Sockets Layer) was introduced by Netscape in the mid-1990s as the first protocol to secure internet communications using encryption. TLS (Transport Layer Security) emerged in 1999 as the standardized successor to SSL, addressing vulnerabilities and enhancing cryptographic algorithms to ensure stronger data integrity and privacy. Over time, SSL versions became deprecated, with TLS evolving through multiple versions (TLS 1.0, 1.1, 1.2, and 1.3) to meet increasing security demands in web and email communications.
Core Functionality and Protocol Differences
TLS (Transport Layer Security) and SSL (Secure Sockets Layer) both provide encryption to secure data transmission over networks, ensuring confidentiality and integrity between client and server. TLS is the successor to SSL, offering improved cryptographic algorithms, enhanced security features, and more efficient handshake protocols to prevent vulnerabilities like POODLE and BEAST attacks. The primary protocol differences include TLS supporting stronger cipher suites, use of HMAC for message authentication, and a more robust key exchange mechanism compared to SSL's outdated methods.
Encryption Algorithms: TLS vs SSL
TLS employs advanced encryption algorithms like AES and ChaCha20, offering stronger security compared to SSL's older algorithms such as RC4 and 3DES. TLS supports modern key exchange methods including Elliptic Curve Diffie-Hellman (ECDHE) for perfect forward secrecy, whereas SSL relies on weaker, outdated mechanisms. The enhanced encryption protocols in TLS ensure better data integrity and confidentiality across secure communications.
Security Vulnerabilities and Risks
TLS (Transport Layer Security) addresses many security vulnerabilities found in its predecessor, SSL (Secure Sockets Layer), by providing stronger encryption algorithms and improved handshake protocols to prevent attacks such as POODLE and BEAST. SSL versions, particularly SSL 2.0 and 3.0, are susceptible to numerous risks including protocol downgrade attacks and weak cipher suites that compromise data integrity and confidentiality. Modern implementations favor TLS 1.2 and TLS 1.3, which mitigate risks through forward secrecy, enhanced message authentication, and resistance to known cryptographic attacks.
Handshake Process Comparison
The TLS handshake process enhances security by employing stronger cryptographic algorithms and key exchange mechanisms compared to SSL, reducing vulnerabilities such as the POODLE attack. TLS negotiates supported cipher suites, exchanges certificates, and performs key exchange using ephemeral keys to enable forward secrecy, whereas SSL relies on outdated algorithms and static keys. This evolution in handshake complexity and cryptographic robustness makes TLS the preferred protocol for secure communications over SSL.
Performance and Compatibility Considerations
TLS offers improved performance over SSL through more efficient handshake protocols and reduced computational overhead, resulting in faster connection establishment and lower latency. TLS is widely supported across modern browsers, servers, and devices, ensuring broad compatibility, whereas SSL is deprecated and limited to legacy systems. Choosing TLS enhances security while maintaining optimal performance and extensive interoperability in current network environments.
Certificate Management in TLS and SSL
TLS enhances certificate management by supporting stronger cryptographic algorithms and automated certificate renewals through protocols like ACME, reducing risks of expired certificates. SSL, being outdated, lacks robust mechanisms for certificate validation and management, often requiring manual updates prone to errors. The transition to TLS is critical for secure certificate lifecycle management and improved trust establishment in digital communications.
Industry Adoption and Best Practices
TLS has largely replaced SSL as the industry standard for securing online communications due to its enhanced encryption algorithms and improved security features. Major organizations and regulatory bodies mandate the use of TLS 1.2 or higher to ensure compliance with best practices and protect sensitive data from vulnerabilities present in SSL protocols. Continuous updates and certificate management within TLS frameworks are critical for maintaining robust cybersecurity defenses in modern enterprise environments.
Future Trends: The Move Beyond SSL
Future trends indicate a clear transition from SSL to TLS protocols as the internet prioritizes enhanced security and encryption standards. TLS 1.3, with faster handshakes and improved cipher suites, is rapidly becoming the industry standard, rendering SSL obsolete due to its vulnerabilities. Emerging technologies such as quantum-resistant cryptography are being integrated into TLS frameworks to safeguard data against evolving cyber threats.
Handshake Protocol
The TLS handshake protocol enhances security by using stronger encryption algorithms and improved key exchange mechanisms compared to the outdated SSL handshake protocol.
Cipher Suite
TLS offers stronger, more secure cipher suites compared to SSL by supporting advanced encryption algorithms and improved key exchange mechanisms.
X.509 Certificate
TLS uses X.509 certificates to securely authenticate servers and encrypt data, improving upon SSL's outdated protocols with enhanced cryptographic standards and certificate validation processes.
Forward Secrecy
TLS provides enhanced Forward Secrecy compared to SSL by using ephemeral key exchanges that prevent session key compromise even if long-term keys are exposed.
Record Layer
TLS Record Layer enhances security and efficiency by using modern encryption algorithms and integrity checks, replacing the older SSL Record Layer protocol vulnerable to attacks.
Session Resumption
TLS improves session resumption by using session tickets and abbreviated handshakes, providing faster reconnections and stronger security compared to the outdated SSL protocols.
PKI (Public Key Infrastructure)
TLS enhances PKI security by using stronger encryption algorithms and improved certificate validation compared to SSL.
Protocol Downgrade Attack
TLS mitigates Protocol Downgrade Attacks more effectively than SSL by enforcing stronger cryptographic versions and supporting mechanisms like TLS_FALLBACK_SCSV to prevent attackers from forcing connections to use weaker protocols.
Mutual Authentication
Mutual authentication in TLS involves both client and server verifying each other's identities using digital certificates, providing enhanced security compared to SSL, which primarily focuses on server authentication.
RC4 Deprecation
TLS has deprecated the insecure RC4 cipher due to vulnerabilities, while SSL protocols inherently rely on vulnerable ciphers including RC4 and are considered obsolete.
TLS vs SSL Infographic
 njnir.com
njnir.com