Secure by Design emphasizes building software with security integrated from the initial development stages, ensuring vulnerabilities are minimized through proactive architecture and coding practices. Secure by Default ensures that software ships with the safest possible settings and configurations out of the box, reducing risks for end users who may not adjust security parameters. Combining both approaches results in robust software that maintains strong security principles internally while protecting users through stringent default protections.
Table of Comparison
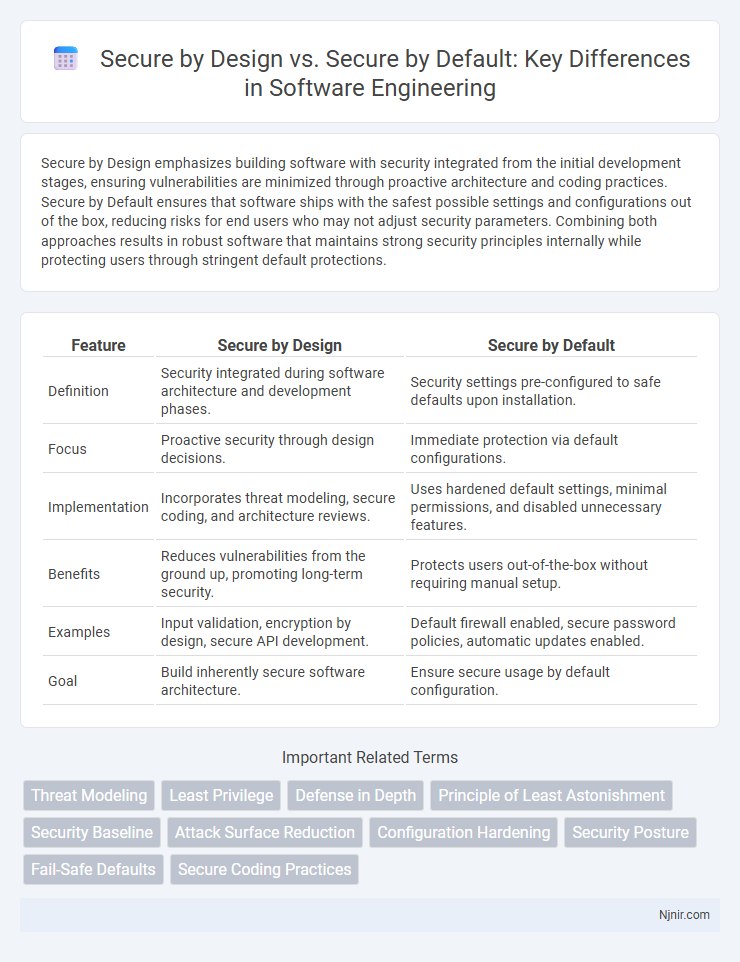
| Feature | Secure by Design | Secure by Default |
|---|---|---|
| Definition | Security integrated during software architecture and development phases. | Security settings pre-configured to safe defaults upon installation. |
| Focus | Proactive security through design decisions. | Immediate protection via default configurations. |
| Implementation | Incorporates threat modeling, secure coding, and architecture reviews. | Uses hardened default settings, minimal permissions, and disabled unnecessary features. |
| Benefits | Reduces vulnerabilities from the ground up, promoting long-term security. | Protects users out-of-the-box without requiring manual setup. |
| Examples | Input validation, encryption by design, secure API development. | Default firewall enabled, secure password policies, automatic updates enabled. |
| Goal | Build inherently secure software architecture. | Ensure secure usage by default configuration. |
Introduction to Secure by Design and Secure by Default
Secure by Design emphasizes integrating security measures directly into the development process, ensuring software architecture inherently mitigates vulnerabilities. Secure by Default prioritizes configuring systems with the highest security settings from the outset, minimizing the risk posed by user misconfigurations or weak settings. Both principles work synergistically to establish robust, resilient systems by addressing security proactively in design and deployment phases.
Key Principles of Secure by Design
Secure by Design emphasizes integrating security into every phase of the software development lifecycle, including threat modeling, secure coding practices, rigorous testing, and regular security assessments. Core principles include minimizing attack surfaces, enforcing least privilege access controls, and implementing defense-in-depth strategies to anticipate and mitigate potential vulnerabilities. This proactive approach contrasts with Secure by Default, which aims to ensure systems are safe out-of-the-box but may rely on pre-configured settings rather than embedded security engineering.
Fundamentals of Secure by Default
Secure by Default emphasizes configuring systems with the highest security settings activated from the start, reducing the attack surface by disabling unnecessary features and services. This fundamental approach ensures that users inherit a secure environment without needing to modify default settings, minimizing human error and misconfigurations. Key principles include strict access controls, encrypted communications, and automatic updates to maintain security resilience over time.
Differences Between Secure by Design and Secure by Default
Secure by Design emphasizes integrating security measures during the initial development phase, ensuring systems are inherently resistant to vulnerabilities from the ground up. Secure by Default focuses on configuring systems with the most secure settings out-of-the-box, minimizing risks without requiring additional user intervention. The key difference lies in Secure by Design's proactive approach in building security into the architecture, whereas Secure by Default prioritizes secure initial configurations and usability for end-users.
Benefits of Secure by Design in Software Engineering
Secure by Design in software engineering integrates security principles throughout the development lifecycle, minimizing vulnerabilities from the outset and reducing costly post-release fixes. This proactive approach enhances system reliability and protects sensitive data by embedding security controls directly into the architecture and code. Consequently, organizations achieve stronger compliance with regulatory standards and foster user trust through inherently resilient software solutions.
Advantages of Secure by Default Approaches
Secure by Default approaches ensure systems are configured with the highest security settings from the outset, minimizing potential vulnerabilities and reducing the need for manual adjustments. This proactive security posture decreases the likelihood of misconfigurations that attackers commonly exploit, enhancing overall system resilience. Enforcing secure defaults streamlines compliance with industry regulations and promotes consistent security standards across deployments.
Challenges in Implementing Both Strategies
Implementing Secure by Design requires integrating security measures from the initial stages of software development, posing challenges in aligning development timelines with comprehensive threat modeling and secure coding practices. Secure by Default mandates pre-configured, hardened settings to minimize vulnerabilities, often conflicting with user flexibility and necessitating extensive testing to balance usability with protection. Both strategies demand continuous maintenance and updated security knowledge, which can strain resources and complicate adoption in fast-paced development environments.
Real-world Examples of Secure by Design vs Secure by Default
Secure by Design involves embedding security principles during the development phase, exemplified by Google's Android OS, which integrates sandboxing and permission models to prevent unauthorized access from the outset. Secure by Default emphasizes configuring systems with the safest settings from installation, as seen in modern Linux distributions like Ubuntu, which disable root access and unnecessary services by default to minimize vulnerabilities. Real-world success depends on combining both approaches, such as Microsoft Windows 10 enforcing secure defaults while encouraging developers to adopt secure coding standards.
Best Practices for Combining Both Approaches
Implementing Secure by Design involves integrating security principles from the initial stages of system development, ensuring robust architecture and threat modeling to prevent vulnerabilities. Secure by Default focuses on configuring systems with the most restrictive settings out-of-the-box, minimizing exposure and requiring explicit permission for access. Combining both approaches requires adopting a proactive security mindset that embeds protective measures in code and infrastructure while ensuring default configurations enforce least privilege, reducing attack surfaces and enhancing overall system resilience.
Future Trends in Secure Software Development
Future trends in secure software development emphasize Secure by Design principles, embedding security measures early in the software development lifecycle to prevent vulnerabilities. Secure by Default ensures that applications ship with the most restrictive settings, minimizing exposure to attacks and simplifying compliance with evolving cybersecurity regulations. Advances in AI-driven development and automated security testing tools are enhancing both approaches, enabling continuous threat detection and proactive risk mitigation.
Threat Modeling
Secure by Design integrates threat modeling into the software development lifecycle to proactively identify and mitigate risks, while Secure by Default configures systems with the safest settings initially, minimizing vulnerabilities without requiring user intervention.
Least Privilege
Secure by Design incorporates the principle of Least Privilege from the outset by architecting systems to minimize access rights, while Secure by Default ensures systems are configured with minimal privileges out-of-the-box to reduce potential security risks.
Defense in Depth
Defense in Depth strengthens cybersecurity by integrating Secure by Design principles that embed security from the development phase and Secure by Default settings that activate comprehensive protections without user intervention.
Principle of Least Astonishment
Secure by Design incorporates the Principle of Least Astonishment by ensuring system behaviors align with user expectations, while Secure by Default enforces this principle through preconfigured, minimally surprising security settings.
Security Baseline
Secure by Design integrates security principles into the development process, while Secure by Default ensures systems adhere to a stringent security baseline upon deployment.
Attack Surface Reduction
Secure by Design minimizes attack surface through proactive architecture and coding practices, while Secure by Default reduces exposure by enabling the most restrictive security settings out-of-the-box.
Configuration Hardening
Configuration hardening strengthens Secure by Default practices by ensuring systems are pre-configured with minimal vulnerabilities, while Secure by Design incorporates security principles inherently during system development to prevent weaknesses.
Security Posture
Secure by Design integrates security measures during system development to strengthen security posture, while Secure by Default ensures out-of-the-box configurations minimize vulnerabilities, collectively enhancing an organization's overall security posture.
Fail-Safe Defaults
Secure by Design emphasizes integrating Fail-Safe Defaults during development to ensure systems inherently restrict access to minimize risks, while Secure by Default configures deployed systems with these protective settings enabled to maintain security without user intervention.
Secure Coding Practices
Secure Coding Practices emphasize Secure by Design principles by integrating security measures during software architecture development rather than relying solely on Secure by Default configurations to mitigate vulnerabilities post-deployment.
Secure by Design vs Secure by Default Infographic
 njnir.com
njnir.com