Intel SGX offers secure enclaves for application-level data protection, enabling isolated execution environments that safeguard sensitive computations from privileged software attacks. AMD SEV provides full virtual machine memory encryption, protecting entire guest VMs from unauthorized access by the hypervisor or other software layers. While SGX targets granular, application-specific security, SEV emphasizes comprehensive VM-level isolation, making each suitable for different threat models and performance considerations in secure computing.
Table of Comparison
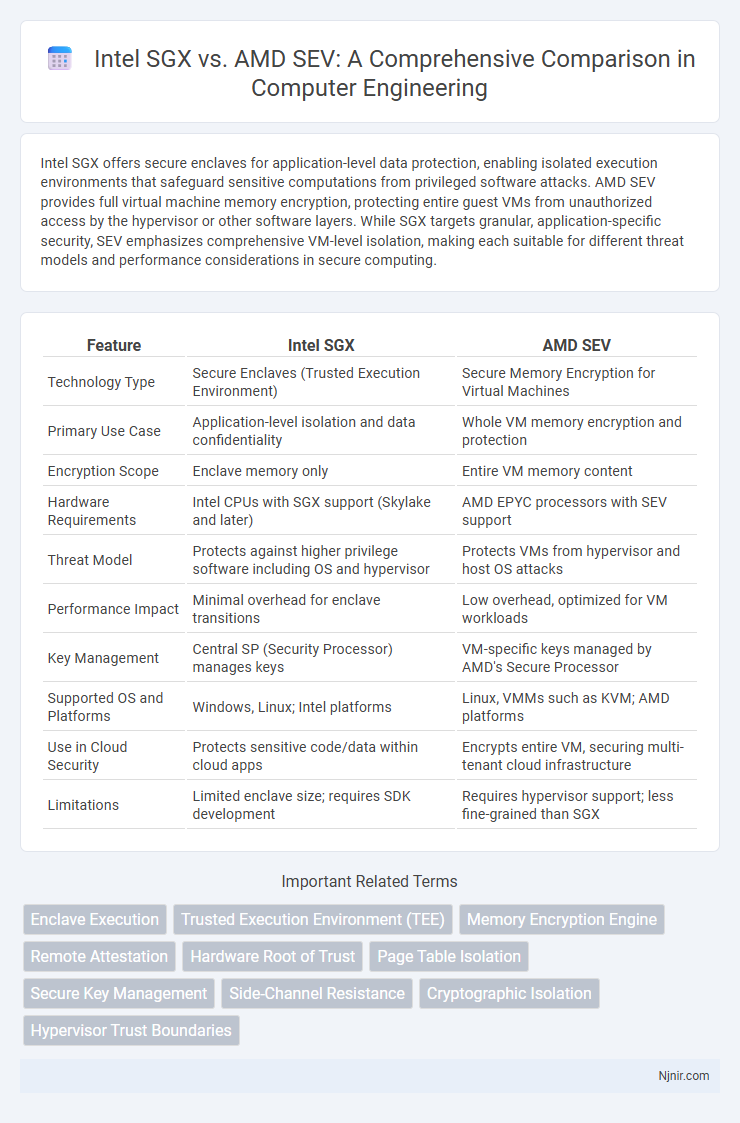
| Feature | Intel SGX | AMD SEV |
|---|---|---|
| Technology Type | Secure Enclaves (Trusted Execution Environment) | Secure Memory Encryption for Virtual Machines |
| Primary Use Case | Application-level isolation and data confidentiality | Whole VM memory encryption and protection |
| Encryption Scope | Enclave memory only | Entire VM memory content |
| Hardware Requirements | Intel CPUs with SGX support (Skylake and later) | AMD EPYC processors with SEV support |
| Threat Model | Protects against higher privilege software including OS and hypervisor | Protects VMs from hypervisor and host OS attacks |
| Performance Impact | Minimal overhead for enclave transitions | Low overhead, optimized for VM workloads |
| Key Management | Central SP (Security Processor) manages keys | VM-specific keys managed by AMD's Secure Processor |
| Supported OS and Platforms | Windows, Linux; Intel platforms | Linux, VMMs such as KVM; AMD platforms |
| Use in Cloud Security | Protects sensitive code/data within cloud apps | Encrypts entire VM, securing multi-tenant cloud infrastructure |
| Limitations | Limited enclave size; requires SDK development | Requires hypervisor support; less fine-grained than SGX |
Introduction to Trusted Execution Environments (TEEs)
Trusted Execution Environments (TEEs) provide isolated, secure areas within a processor to protect sensitive code and data from unauthorized access. Intel SGX (Software Guard Extensions) creates small, hardware-protected enclaves that ensure confidentiality and integrity for critical applications, while AMD SEV (Secure Encrypted Virtualization) encrypts entire virtual machine memory to safeguard workloads in virtualized environments. Both technologies enhance cloud security by enabling confidential computing, but they differ in granularity and scope of protection, with SGX focusing on enclave-level isolation and SEV on VM-level encryption.
Overview of Intel SGX: Architecture and Features
Intel SGX (Software Guard Extensions) is a hardware-based security technology that creates isolated enclaves within the CPU to protect sensitive code and data from unauthorized access, even with system-level privileges. Its architecture leverages a trusted execution environment (TEE) to ensure data confidentiality and integrity by encrypting enclave memory and providing attestation mechanisms. Key features include enclave isolation, memory encryption, remote attestation, and support for secure key management, making it ideal for protecting sensitive workloads in cloud and enterprise environments.
Overview of AMD SEV: Architecture and Features
AMD SEV (Secure Encrypted Virtualization) leverages hardware-based memory encryption to protect virtual machines by isolating their memory from the hypervisor and other VMs, using a dedicated Secure Processor and Secure Memory Encryption engine. Its architecture supports full memory encryption with dynamically generated keys for each VM, enabling confidentiality and integrity without compromising performance. SEV's features include secure key management, hardware root of trust, and support for live migration of encrypted VMs, positioning it as a robust solution for cloud security.
Security Models: Comparing SGX and SEV
Intel SGX utilizes a hardware-based Trusted Execution Environment (TEE) that isolates specific application enclaves, protecting code and data against unauthorized access even from privileged system software. AMD SEV employs memory encryption at the virtual machine level, encrypting the entire guest memory to secure workloads in multi-tenant environments without requiring application modifications. Both security models emphasize data confidentiality and integrity, but SGX targets fine-grained enclave protection while SEV offers broader virtual machine isolation with scalable encryption mechanisms.
Performance Impact: Intel SGX vs. AMD SEV
Intel SGX performs enclave-based secure computing with minimal overhead for small memory sizes but faces increased latency and reduced throughput as enclave size grows due to frequent memory paging. AMD SEV encrypts entire virtual machines, offering near-native performance with low overhead on CPU and memory operations, making it more scalable for larger workloads. Benchmark analyses consistently show AMD SEV maintains higher throughput and lower latency under heavy workloads compared to Intel SGX's constrained enclave limits.
Application Use Cases and Limitations
Intel SGX enables fine-grained application enclave protection ideal for securing sensitive computations in cloud environments, including confidential AI model processing and secure data analytics. AMD SEV offers broader VM-level encryption suitable for protecting entire virtual machines, making it effective for multi-tenant cloud infrastructure and legacy application isolation without significant code modification. Intel SGX faces limitations with enclave size and complex memory management, while AMD SEV struggles with finer-grained attestation and may expose applications to increased attack surface due to larger trusted computing base.
Memory Protection and Encryption Mechanisms
Intel SGX employs hardware-based memory encryption and isolation through secure enclaves, protecting specific application memory regions from unauthorized access even by the OS or hypervisor. AMD SEV uses full memory encryption with separate keys for each virtual machine, ensuring that guest memory is protected from other VMs and the hypervisor by encrypting the entire VM memory content. Both technologies leverage hardware-level cryptographic engines but differ in granularity: SGX focuses on enclave-based application-level protection, while SEV provides broader VM-level protection for cloud and virtualization environments.
Developer Experience and Ecosystem Support
Intel SGX offers developers fine-grained, application-level enclave isolation with mature SDKs and extensive documentation that facilitate secure coding and debugging, supported by a broad ecosystem including cloud providers and security tools. AMD SEV provides transparent virtualization-based memory encryption with less developer intervention required, supported by hypervisor integrations primarily aimed at protecting entire VM environments rather than individual applications. Ecosystem support for Intel SGX is more established, with a wider range of libraries, frameworks, and community resources, whereas AMD SEV is growing but still more limited in developer tooling and application-specific support.
Real-World Deployments and Industry Adoption
Intel SGX has seen widespread real-world deployment in cloud computing environments, particularly for secure enclaves protecting sensitive data in applications like confidential AI inference and secure multi-party computations. AMD SEV is increasingly adopted in virtualization platforms, enabling encrypted virtual machines that protect workloads in multi-tenant cloud infrastructures with minimal performance overhead. Industry adoption favors Intel SGX for fine-grained application enclave security, while AMD SEV gains traction for broader VM-level encryption in enterprise cloud services.
Future Trends in Hardware-Based Security
Intel SGX and AMD SEV represent key innovations in hardware-based security, with Intel SGX focusing on secure enclaves for isolated execution and AMD SEV providing full memory encryption for virtual machines. Future trends emphasize enhanced scalability, interoperability between different security architectures, and integration with emerging technologies like confidential computing in cloud environments. Advances in firmware validation and real-time threat detection will drive more robust protection against increasingly sophisticated attacks.
Enclave Execution
Intel SGX provides hardware-based enclave execution with fine-grained memory isolation for secure application code, while AMD SEV offers full virtual machine encryption to protect entire workloads at the hypervisor level.
Trusted Execution Environment (TEE)
Intel SGX provides hardware-based Trusted Execution Environments with enclave isolation for secure code execution, while AMD SEV offers memory encryption to protect virtual machines, enabling broader TEE protection in cloud environments.
Memory Encryption Engine
Intel SGX utilizes the Memory Encryption Engine (MEE) to encrypt specific enclave memory regions, whereas AMD SEV employs full memory encryption at the hypervisor level to protect entire virtual machines.
Remote Attestation
Intel SGX offers fine-grained enclave-level remote attestation for verifying trusted execution environments, while AMD SEV provides VM-level remote attestation ensuring entire virtual machine integrity.
Hardware Root of Trust
Intel SGX utilizes a dedicated hardware root of trust embedded in the CPU to create isolated enclaves, whereas AMD SEV relies on a secure processor-based root of trust to encrypt virtual machine memory, ensuring hardware-level data confidentiality.
Page Table Isolation
Intel SGX provides fine-grained Page Table Isolation by encrypting enclave memory and limiting page table access, whereas AMD SEV secures virtual machine memory through hardware encryption but relies on hypervisor-managed page tables without direct enclave-level isolation.
Secure Key Management
Intel SGX provides hardware-based secure key management within isolated enclaves, while AMD SEV offers encrypted memory protection with secure key handling managed by the AMD Secure Processor.
Side-Channel Resistance
Intel SGX offers hardware-based isolation with limited side-channel resistance, while AMD SEV provides broader memory encryption and stronger protection against side-channel attacks in virtualized environments.
Cryptographic Isolation
Intel SGX provides fine-grained cryptographic isolation at the application level through secure enclaves, while AMD SEV offers hardware-based full VM memory encryption ensuring cryptographic isolation at the virtual machine level.
Hypervisor Trust Boundaries
Intel SGX confines sensitive computations within secure enclaves isolated from the hypervisor, while AMD SEV encrypts virtual machine memory to protect against hypervisor-level threats, redefining hypervisor trust boundaries by enabling confidential computing in different architectural layers.
Intel SGX vs AMD SEV Infographic
 njnir.com
njnir.com