JWTs enable stateless authentication by storing user data in a JSON Web Token, which eliminates the need for server-side session storage and improves scalability. Session cookies rely on server-maintained session data, offering more control and easier invalidation but can increase server memory usage. Choosing between JWTs and session cookies depends on the application's requirements for scalability, security, and ease of session management.
Table of Comparison
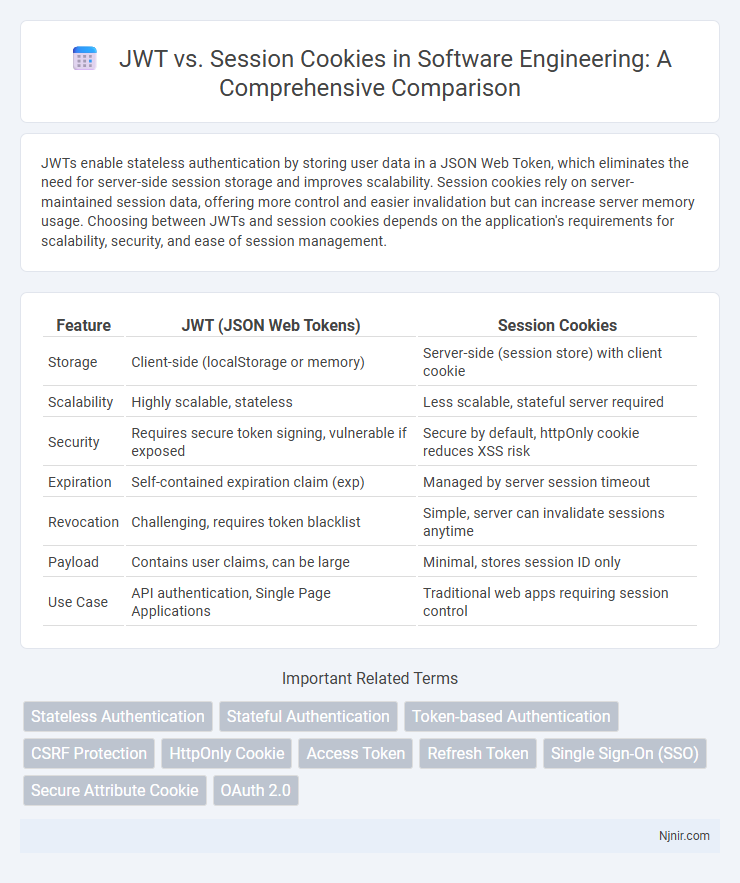
| Feature | JWT (JSON Web Tokens) | Session Cookies |
|---|---|---|
| Storage | Client-side (localStorage or memory) | Server-side (session store) with client cookie |
| Scalability | Highly scalable, stateless | Less scalable, stateful server required |
| Security | Requires secure token signing, vulnerable if exposed | Secure by default, httpOnly cookie reduces XSS risk |
| Expiration | Self-contained expiration claim (exp) | Managed by server session timeout |
| Revocation | Challenging, requires token blacklist | Simple, server can invalidate sessions anytime |
| Payload | Contains user claims, can be large | Minimal, stores session ID only |
| Use Case | API authentication, Single Page Applications | Traditional web apps requiring session control |
Understanding JWT and Session Cookies
JWT (JSON Web Token) is a compact, URL-safe token that securely transmits claims between parties, often used for stateless authentication by embedding user information within the token payload. Session cookies store a unique session identifier on the client side and maintain server-side session data, enabling stateful user authentication and easier session invalidation. Understanding the core difference highlights JWT's self-contained nature versus session cookies' reliance on server-side storage to manage user sessions.
How JWT Works in Authentication
JWT (JSON Web Token) works in authentication by securely transmitting user identity information between client and server using a digitally signed token. When a user logs in, the server generates a JWT containing claims such as user ID and expiration time, which is sent to the client and stored (typically in local storage or cookies). On subsequent requests, the client includes the JWT in the Authorization header, allowing the server to verify the token's signature and validate the user's session without maintaining server-side state.
How Session Cookies Manage User Sessions
Session cookies store a unique session ID on the client side, linking it to server-stored session data that tracks user authentication and preferences. The server maintains the session state, enabling quick verification and seamless management of user interactions without exposing sensitive information. This approach enhances security by centralizing control over session expiration, invalidation, and data consistency during user sessions.
Security Considerations: JWT vs Session Cookies
JWTs store user data in a digitally signed token that can be verified without server-side storage, reducing server load but increasing exposure if tokens are intercepted or stolen. Session cookies rely on server-side session storage and use HttpOnly and Secure flags to protect against XSS and CSRF attacks, offering tighter control over session invalidation and expiration. JWTs require careful implementation of token expiration and storage practices to mitigate risks, while session cookies benefit from well-established security mechanisms inherent in browser cookie management.
Scalability: Which Approach Handles Growth Better?
JWTs offer better scalability for growing applications by enabling stateless authentication, which eliminates the need for server-side session storage and reduces database load. Session cookies require maintaining session data on the server, leading to increased memory usage and potential bottlenecks as user numbers rise. This makes JWTs more efficient in handling spike traffic and distributing load across multiple servers or microservices.
Performance Impact Analysis
JWTs reduce server memory usage by storing token data client-side, enabling stateless authentication and faster scalability in distributed systems. Session cookies require server-side storage, which can increase memory consumption and response latency as user sessions grow. However, JWTs may incur larger payload sizes affecting network transmission time, while session cookies typically have smaller size but can cause bottlenecks due to centralized session management.
Use Cases: When to Use JWT vs Session Cookies
JWTs excel in stateless authentication scenarios, ideal for RESTful APIs, mobile apps, and single-page applications where scalability and cross-domain authentication are critical. Session cookies provide robust security suited for traditional web applications requiring server-side session management, such as banking sites or intranet portals with sensitive data and frequent session validation. Use JWTs for decentralized, token-based access control and session cookies for centralized, server-managed user sessions with strict security policies.
Implementation Challenges and Pitfalls
Implementing JWT tokens often involves managing stateless authentication, which can lead to challenges like token revocation and token storage security on the client side, increasing risks of token theft or misuse. Session cookies rely on server-side storage, requiring careful session management to prevent issues such as session fixation, cross-site request forgery (CSRF), and scaling complexities in distributed environments. Both approaches demand robust protection mechanisms, including secure transmission (HTTPS), proper expiration handling, and mitigation against common vulnerabilities related to token/session hijacking.
Common Vulnerabilities and How to Mitigate Them
JWTs are vulnerable to token theft, replay attacks, and algorithm manipulation, mitigated by using strong signing algorithms like RS256, secure storage such as HTTP-only cookies, and implementing token expiration with refresh mechanisms. Session cookies face risks including cross-site scripting (XSS), cross-site request forgery (CSRF), and session fixation, addressable by applying HttpOnly and Secure flags, using same-site cookie attributes, and regenerating session IDs after login. Both require careful handling of sensitive data and strict validation to prevent unauthorized access and maintain secure authentication flows.
Best Practices for Secure Session Management
Secure session management favors short-lived JWTs with rotating refresh tokens to minimize replay attack risks and enforce strict expiration policies. Session cookies should use HttpOnly, Secure, and SameSite attributes to protect against XSS and CSRF vulnerabilities while storing minimal sensitive information. Implementing server-side token validation and proper logout mechanisms ensures robust protection against session hijacking in both JWT and session cookie approaches.
Stateless Authentication
JWT enables stateless authentication by embedding user data and session information within the token itself, eliminating the need for server-side session storage required by traditional session cookies.
Stateful Authentication
Session cookies enable stateful authentication by storing user session data on the server, providing enhanced security and easier session invalidation compared to stateless JWT-based authentication.
Token-based Authentication
Token-based authentication using JWT enables stateless, scalable user verification by securely encoding user data and expiration directly in the token, eliminating the need for server-side session storage unlike traditional session cookies.
CSRF Protection
JWTs mitigate CSRF attacks by storing tokens in secure HTTP-only cookies or using the Authorization header, whereas traditional session cookies require CSRF tokens to prevent unauthorized requests.
HttpOnly Cookie
HttpOnly cookies enhance security for session management by preventing client-side scripts from accessing JWT or session tokens, mitigating XSS attacks.
Access Token
Access tokens in JWT provide stateless, scalable authentication by securely encoding user information, unlike session cookies that rely on server-side storage and session management.
Refresh Token
Refresh tokens in JWT-based authentication enable secure, stateless access token renewal without requiring server-side session storage, unlike traditional session cookies that maintain state through server-held session identifiers.
Single Sign-On (SSO)
JWT enables stateless Single Sign-On (SSO) by securely transmitting user identity across multiple domains without server-side session storage required by traditional session cookies.
Secure Attribute Cookie
The Secure attribute in cookies ensures session cookies are transmitted only over HTTPS, enhancing security compared to JWTs which rely on token integrity but do not inherently enforce secure transmission.
OAuth 2.0
OAuth 2.0 commonly uses JWTs for stateless, scalable token-based authentication, whereas session cookies rely on server-side session storage, making JWTs preferable for distributed systems.
JWT vs session cookies Infographic
 njnir.com
njnir.com