Static Application Security Testing (SAST) analyzes source code for vulnerabilities without executing the program, enabling early detection of security flaws during development. Dynamic Application Security Testing (DAST) examines running applications through simulated attacks to identify runtime vulnerabilities and weaknesses that may not be visible in source code. Combining SAST and DAST provides a comprehensive security assessment by covering both internal code issues and external runtime threats.
Table of Comparison
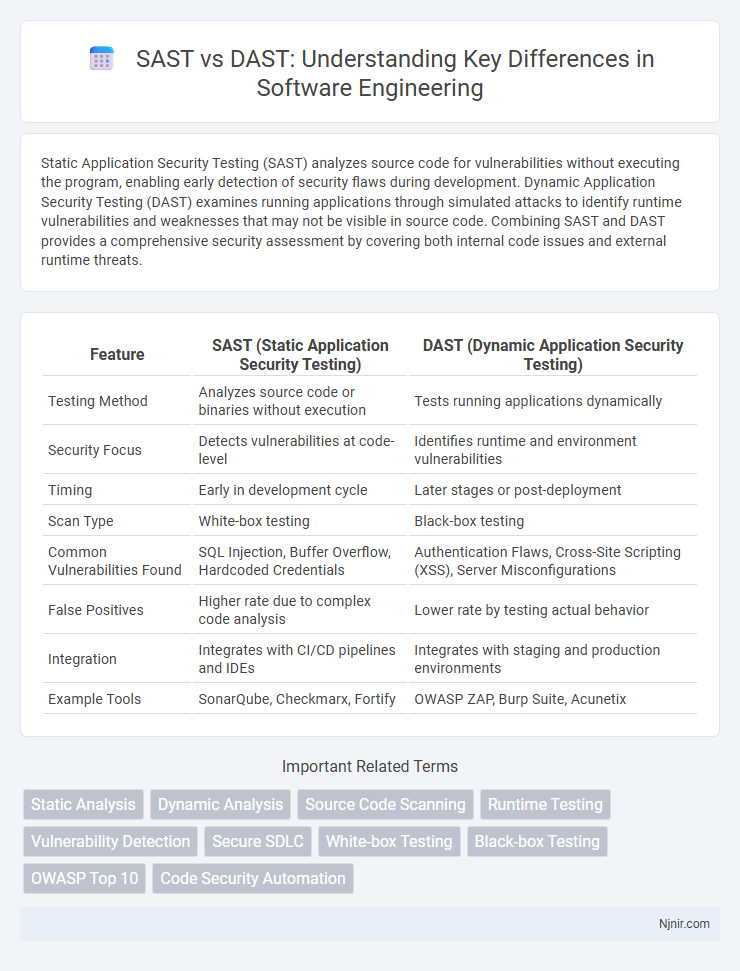
| Feature | SAST (Static Application Security Testing) | DAST (Dynamic Application Security Testing) |
|---|---|---|
| Testing Method | Analyzes source code or binaries without execution | Tests running applications dynamically |
| Security Focus | Detects vulnerabilities at code-level | Identifies runtime and environment vulnerabilities |
| Timing | Early in development cycle | Later stages or post-deployment |
| Scan Type | White-box testing | Black-box testing |
| Common Vulnerabilities Found | SQL Injection, Buffer Overflow, Hardcoded Credentials | Authentication Flaws, Cross-Site Scripting (XSS), Server Misconfigurations |
| False Positives | Higher rate due to complex code analysis | Lower rate by testing actual behavior |
| Integration | Integrates with CI/CD pipelines and IDEs | Integrates with staging and production environments |
| Example Tools | SonarQube, Checkmarx, Fortify | OWASP ZAP, Burp Suite, Acunetix |
Introduction to Application Security Testing
Static Application Security Testing (SAST) analyzes source code or binaries early in the software development lifecycle to identify vulnerabilities like SQL injection, buffer overflows, and insecure coding practices. Dynamic Application Security Testing (DAST) examines running applications by simulating external attacks to detect issues such as authentication flaws, cross-site scripting (XSS), and runtime errors. Both SAST and DAST are critical components of application security testing that provide complementary insights, enhancing overall risk detection and mitigation efforts.
What is SAST (Static Application Security Testing)?
Static Application Security Testing (SAST) is a white-box testing method that analyzes source code, bytecode, or binaries for security vulnerabilities without executing the program. It provides early detection of issues such as SQL injection, buffer overflows, and cross-site scripting by scanning the application's internal structure during development. SAST tools integrate into the software development lifecycle to enable continuous security assessment and code quality improvement before deployment.
How DAST (Dynamic Application Security Testing) Works
DAST (Dynamic Application Security Testing) analyzes a running application by simulating external attacks to identify security vulnerabilities in real-time. It interacts with the application through its web interface, scanning for issues such as SQL injection, cross-site scripting (XSS), and insecure server configurations without access to the source code. This approach provides insights into runtime behavior and security flaws that manifest during actual application execution.
Key Differences Between SAST and DAST
SAST (Static Application Security Testing) analyzes source code or binaries at rest to identify vulnerabilities early in the development lifecycle, while DAST (Dynamic Application Security Testing) examines running applications to detect security flaws during runtime. SAST offers white-box testing with access to internal code structures, enabling detection of issues like SQL injection and buffer overflows before deployment, whereas DAST performs black-box testing, simulating external attacks without source code access. The key differences include timing in the SDLC, level of code visibility, and types of vulnerabilities identified, making SAST ideal for early code review and DAST crucial for runtime threat detection.
Advantages of SAST in Software Development
SAST (Static Application Security Testing) provides early vulnerability detection by analyzing source code before runtime, allowing developers to identify and resolve security issues during the coding phase. It offers comprehensive coverage of code paths, enabling detection of complex logic flaws and insecure coding practices that can be missed by runtime testing. Integrating SAST into the development pipeline reduces remediation costs and accelerates secure software delivery by preventing vulnerabilities prior to deployment.
Benefits and Limitations of DAST
Dynamic Application Security Testing (DAST) identifies runtime vulnerabilities by analyzing an application from the outside while it is running, providing real-world attack simulation benefits. DAST tools excel at detecting issues like SQL injection, cross-site scripting (XSS), and authentication flaws without access to source code, making them suitable for black-box testing. However, DAST limitations include inability to identify hidden code vulnerabilities, dependency on a running application environment, and potential false positives due to limited code visibility.
When to Use SAST vs DAST
SAST (Static Application Security Testing) is best used early in the development lifecycle to identify vulnerabilities in source code before deployment, enabling developers to fix issues during coding. DAST (Dynamic Application Security Testing) is more suitable for testing running applications in a runtime environment, detecting exploitable vulnerabilities that manifest during execution. Employing SAST during development and DAST post-deployment ensures comprehensive security coverage across both code and runtime behavior.
Integration of SAST and DAST in DevSecOps
Integrating SAST (Static Application Security Testing) and DAST (Dynamic Application Security Testing) in DevSecOps enhances the security posture by combining early vulnerability detection with runtime analysis, enabling comprehensive coverage across the software development lifecycle. SAST tools analyze source code to identify flaws before deployment, while DAST examines running applications to catch runtime vulnerabilities, ensuring continuous security validation. This integration supports automated pipelines, accelerates feedback loops, and aligns security testing with agile development practices for robust application security.
Common Pitfalls in SAST and DAST Implementation
Common pitfalls in SAST implementation include false positives that overwhelm developers, lack of integration with CI/CD pipelines, and insufficient coverage of third-party libraries, leading to missed vulnerabilities. In DAST, challenges arise from limited code visibility, difficulty in detecting complex logic flaws, and dependence on accurate test environment configurations, which can result in incomplete security assessments. Both approaches require continuous tuning and collaboration between security and development teams to maximize effectiveness and minimize blind spots.
Best Practices for Combining SAST and DAST
Effective security testing integrates Static Application Security Testing (SAST) and Dynamic Application Security Testing (DAST) to maximize vulnerability detection. Best practices recommend conducting SAST early in the Software Development Life Cycle (SDLC) to identify coding flaws before deployment, while employing DAST in later stages to analyze runtime behavior and uncover runtime vulnerabilities. Combining SAST's comprehensive code coverage with DAST's real-world attack simulations ensures a robust, multi-layered defense strategy that enhances overall application security.
Static Analysis
Static Application Security Testing (SAST) analyzes source code early in the development cycle to identify vulnerabilities, enabling faster and more efficient remediation compared to Dynamic Application Security Testing (DAST).
Dynamic Analysis
Dynamic Application Security Testing (DAST) analyzes running applications to identify security vulnerabilities by simulating external attacks, providing real-time detection of runtime issues that static analysis tools like SAST cannot uncover.
Source Code Scanning
Static Application Security Testing (SAST) analyzes source code or binaries early in development to identify vulnerabilities before deployment, providing precise, code-level insights unlike Dynamic Application Security Testing (DAST) which examines running applications.
Runtime Testing
DAST excels in runtime testing by analyzing applications in their operational environment to identify vulnerabilities that occur during execution.
Vulnerability Detection
Static Application Security Testing (SAST) detects coding vulnerabilities by analyzing source code early in the development cycle, while Dynamic Application Security Testing (DAST) identifies runtime vulnerabilities by assessing the application's behavior during execution.
Secure SDLC
Static Application Security Testing (SAST) identifies code vulnerabilities early in the secure SDLC by analyzing source code, while Dynamic Application Security Testing (DAST) detects runtime security issues through behavioral testing, together ensuring comprehensive threat mitigation.
White-box Testing
White-box testing in SAST analyzes source code for security vulnerabilities by examining internal structures, enabling early detection compared to DAST's runtime, black-box approach.
Black-box Testing
Black-box testing in DAST evaluates application security by analyzing runtime behavior without source code access, unlike SAST which uses static code analysis for vulnerability detection.
OWASP Top 10
SAST analyzes source code for OWASP Top 10 vulnerabilities like injection and broken authentication early in development, while DAST tests running applications to detect runtime security issues such as cross-site scripting and insecure deserialization.
Code Security Automation
SAST analyzes source code for vulnerabilities early in development, while DAST tests running applications to identify security flaws, both crucial for comprehensive code security automation.
SAST vs DAST Infographic
 njnir.com
njnir.com