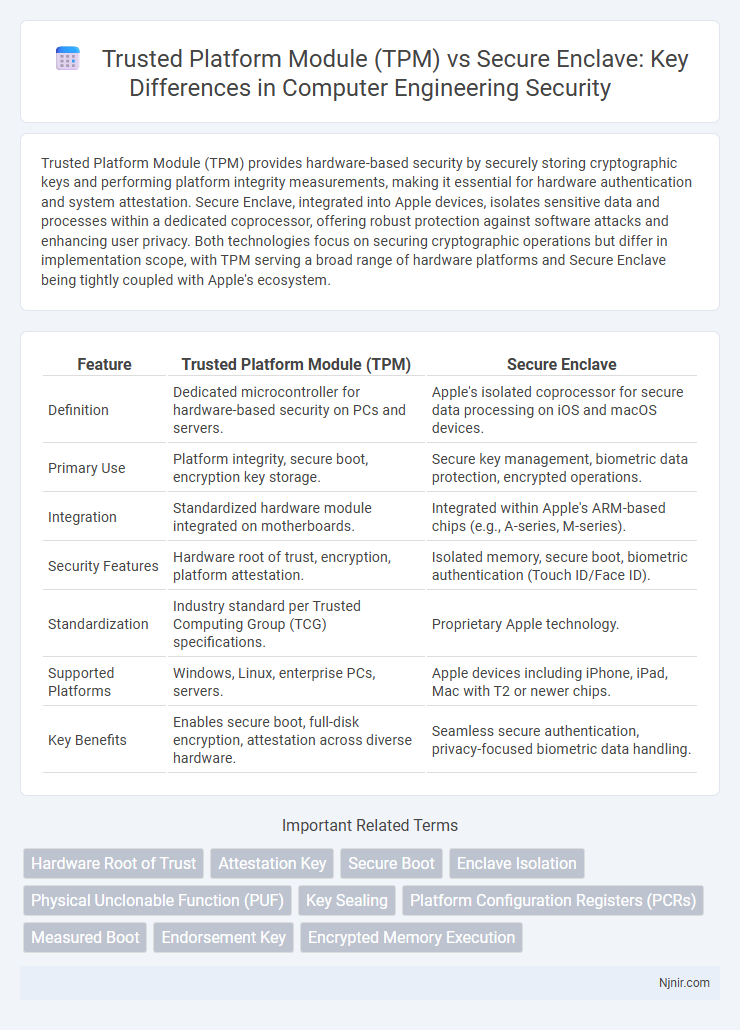
Trusted Platform Module (TPM) provides hardware-based security by securely storing cryptographic keys and performing platform integrity measurements, making it essential for hardware authentication and system attestation. Secure Enclave, integrated into Apple devices, isolates sensitive data and processes within a dedicated coprocessor, offering robust protection against software attacks and enhancing user privacy. Both technologies focus on securing cryptographic operations but differ in implementation scope, with TPM serving a broad range of hardware platforms and Secure Enclave being tightly coupled with Apple's ecosystem.
Table of Comparison
| Feature | Trusted Platform Module (TPM) | Secure Enclave |
|---|---|---|
| Definition | Dedicated microcontroller for hardware-based security on PCs and servers. | Apple's isolated coprocessor for secure data processing on iOS and macOS devices. |
| Primary Use | Platform integrity, secure boot, encryption key storage. | Secure key management, biometric data protection, encrypted operations. |
| Integration | Standardized hardware module integrated on motherboards. | Integrated within Apple's ARM-based chips (e.g., A-series, M-series). |
| Security Features | Hardware root of trust, encryption, platform attestation. | Isolated memory, secure boot, biometric authentication (Touch ID/Face ID). |
| Standardization | Industry standard per Trusted Computing Group (TCG) specifications. | Proprietary Apple technology. |
| Supported Platforms | Windows, Linux, enterprise PCs, servers. | Apple devices including iPhone, iPad, Mac with T2 or newer chips. |
| Key Benefits | Enables secure boot, full-disk encryption, attestation across diverse hardware. | Seamless secure authentication, privacy-focused biometric data handling. |
Introduction to Hardware-Based Security Modules
Trusted Platform Module (TPM) and Secure Enclave are critical hardware-based security modules designed to enhance system integrity and protect sensitive data. TPM, typically integrated into motherboard chips, provides cryptographic functions such as secure key storage, device authentication, and platform integrity verification, widely used in enterprise environments. Secure Enclave, employed in Apple devices, offers a dedicated coprocessor that isolates sensitive operations like biometric data processing and cryptographic tasks, ensuring enhanced protection through hardware-level isolation and encrypted memory.
Overview of Trusted Platform Module (TPM)
The Trusted Platform Module (TPM) is a hardware-based security chip designed to securely generate, store, and manage cryptographic keys, enabling platform integrity and secure boot processes. Integrated into motherboards, TPM provides hardware root of trust, ensuring that sensitive data such as encryption keys and digital certificates are protected from software-based attacks. Widely used in enterprise environments, TPM supports functionalities like disk encryption, device authentication, and attestation for trusted computing.
Overview of Secure Enclave Technology
Secure Enclave technology is a dedicated security coprocessor integrated into Apple devices, designed to safeguard sensitive data such as encryption keys, biometric information, and authentication credentials. It operates independently from the main processor, utilizing a secure boot process and hardware-based encryption to ensure data integrity and confidentiality. Unlike traditional Trusted Platform Modules (TPMs), the Secure Enclave offers tightly integrated security features optimized for biometric authentication and device-specific security protocols within iOS and macOS ecosystems.
Key Architectural Differences: TPM vs Secure Enclave
Trusted Platform Module (TPM) is a discrete hardware chip designed to provide platform integrity by securely storing cryptographic keys and performing cryptographic operations independently of the main CPU. Secure Enclave, proprietary to Apple devices, is a dedicated coprocessor integrated within the SoC that isolates sensitive data and cryptographic functions, enabling secure boot, biometric data protection, and encryption key management. Unlike TPM's standardized external module architecture, Secure Enclave leverages tight integration with the device's processor and iOS, offering enhanced performance and security tailored to Apple's ecosystem.
Security Features Comparison
Trusted Platform Module (TPM) provides hardware-based security by securely storing cryptographic keys, performing platform integrity measurements, and enabling secure boot processes, protecting against firmware and software tampering. Secure Enclave, an isolated coprocessor in Apple devices, offers encrypted data storage, secure key management, and biometric data protection with a dedicated secure environment that runs its own microkernel. While TPM is widely adopted in PCs for device authentication and disk encryption, Secure Enclave delivers enhanced biometric and application-level security within Apple's ecosystem.
Use Cases in Modern Computing
Trusted Platform Module (TPM) primarily secures cryptographic keys and ensures platform integrity in enterprise environments, facilitating hardware-based authentication, disk encryption, and secure boot processes. Secure Enclave, embedded in Apple devices, protects sensitive user data such as biometrics and cryptographic operations within a dedicated, isolated coprocessor, enhancing privacy for mobile and personal computing. Both technologies are essential for trusted computing but differ in scope, with TPM targeting broad hardware security and Secure Enclave focusing on device-specific data protection in modern computing ecosystems.
Performance and Integration Considerations
Trusted Platform Module (TPM) offers hardware-based cryptographic operations optimized for secure key storage and platform integrity verification, delivering consistent performance across diverse hardware environments. Secure Enclave, embedded within Apple devices' SoCs, provides high-speed cryptographic processing tightly integrated with iOS/macOS, enabling lower latency and seamless interaction with system-level security frameworks. Performance comparisons highlight TPM's broader compatibility but limited acceleration, whereas Secure Enclave benefits from specialized silicon acceleration and deep OS integration, impacting choice based on device ecosystem and security requirements.
Vulnerabilities and Attack Surfaces
Trusted Platform Module (TPM) and Secure Enclave both provide hardware-based security, but TPM is more susceptible to firmware attacks and physical tampering due to its integration on the motherboard, while Secure Enclave, integrated within Apple's processors, benefits from isolated execution environments that limit exposure to software exploits. TPM vulnerabilities often include side-channel attacks and hardware rootkit implantation, whereas Secure Enclave faces risks like speculative execution exploits and potential firmware bugs but maintains reduced attack surfaces through stringent access controls. Effective mitigation for both involves regular firmware updates, robust cryptographic protocols, and hardware-based isolation to minimize exploitation risks.
Industry Adoption and Compatibility
Trusted Platform Module (TPM) is widely adopted across enterprise IT and PC manufacturers due to its hardware-based security standard integrated into many Windows devices and servers, ensuring broad compatibility with legacy systems and enterprise security frameworks. Secure Enclave, developed by Apple, is primarily found in iOS and macOS devices, providing isolated cryptographic operations and secure boot processes tailored for Apple's ecosystem, limiting its compatibility outside Apple hardware. Industry adoption favors TPM in multi-vendor environments and enterprise infrastructures, while Secure Enclave excels in consumer devices that require high-level protection within a closed platform.
Future Trends in Hardware Security Modules
Trusted Platform Module (TPM) and Secure Enclave represent pivotal hardware security modules advancing towards enhanced cryptographic functions and isolated execution environments. Future trends indicate increased integration of TPMs with AI-driven threat detection and expansion of Secure Enclave capabilities for confidential computing in cloud and edge devices. Innovations will likely emphasize resilience against quantum attacks and seamless interoperability within multi-layered security architectures.
Hardware Root of Trust
Trusted Platform Module (TPM) provides a standardized hardware root of trust through a dedicated chip for secure cryptographic operations, while Secure Enclave integrates a hardware root of trust within Apple devices for isolated processing and key management.
Attestation Key
Trusted Platform Module (TPM) provides a hardware-based Attestation Key for device identity verification and secure boot processes, while Secure Enclave generates a unique Attestation Key within its isolated environment to authenticate device integrity and enable encrypted communications on Apple devices.
Secure Boot
Secure Boot leverages Trusted Platform Module (TPM) hardware to validate boot integrity, while Secure Enclave provides isolated processing without directly enforcing Secure Boot protocols.
Enclave Isolation
Secure Enclave provides hardware-based enclave isolation with dedicated secure memory and a separate processor for enhanced protection against unauthorized access, whereas Trusted Platform Module (TPM) primarily offers cryptographic functions without isolated execution environments.
Physical Unclonable Function (PUF)
Trusted Platform Module (TPM) primarily relies on integrated circuit-based security without inherent Physical Unclonable Function (PUF) capabilities, whereas Secure Enclave incorporates PUF technology for unique, hardware-rooted cryptographic key generation and enhanced tamper resistance.
Key Sealing
Trusted Platform Module (TPM) secures key sealing by storing cryptographic keys tied to hardware and platform integrity, while Secure Enclave provides isolated key sealing within a dedicated coprocessor to protect sensitive data in Apple devices.
Platform Configuration Registers (PCRs)
Trusted Platform Module (TPM) uses Platform Configuration Registers (PCRs) to securely store cryptographic measurements for device integrity verification, whereas Secure Enclave lacks dedicated PCRs, relying instead on isolated hardware and software environments for secure key management and execution.
Measured Boot
Trusted Platform Module (TPM) provides hardware-based Measured Boot by securely recording boot metrics to ensure system integrity, while Secure Enclave primarily focuses on isolated secure execution without native Measured Boot capabilities.
Endorsement Key
The Trusted Platform Module (TPM) uses an Endorsement Key (EK) as a unique, hardware-embedded asymmetric key to securely identify and authenticate the device, whereas the Secure Enclave generates device-specific cryptographic keys without exposing a persistent, externally verifiable EK.
Encrypted Memory Execution
Secure Enclave utilizes dedicated encrypted memory execution for enhanced security, whereas Trusted Platform Module (TPM) primarily provides cryptographic key storage without direct support for encrypted memory execution.
Trusted Platform Module (TPM) vs Secure Enclave Infographic
 njnir.com
njnir.com