OAuth provides delegated authorization by allowing users to grant third-party applications limited access to their resources without sharing credentials, ideal for API access and mobile apps. SAML is primarily focused on federated single sign-on (SSO) for enterprise environments, enabling secure identity exchange between identity providers and service providers. OAuth excels in authorization scenarios, while SAML is better suited for authentication and identity federation in web-based applications.
Table of Comparison
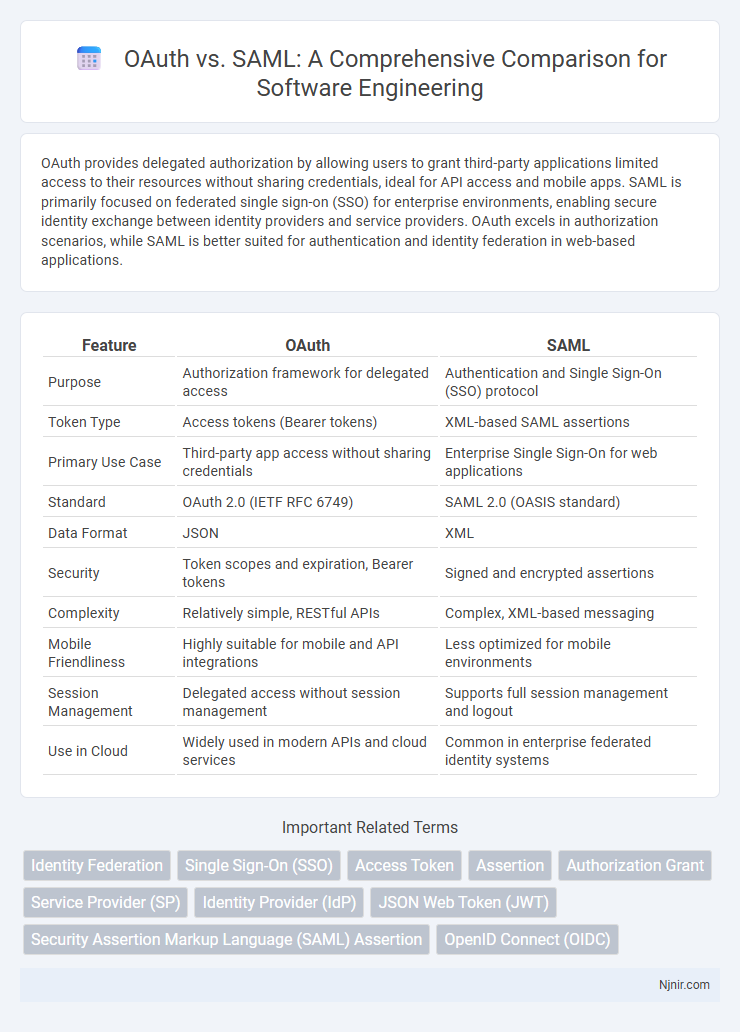
| Feature | OAuth | SAML |
|---|---|---|
| Purpose | Authorization framework for delegated access | Authentication and Single Sign-On (SSO) protocol |
| Token Type | Access tokens (Bearer tokens) | XML-based SAML assertions |
| Primary Use Case | Third-party app access without sharing credentials | Enterprise Single Sign-On for web applications |
| Standard | OAuth 2.0 (IETF RFC 6749) | SAML 2.0 (OASIS standard) |
| Data Format | JSON | XML |
| Security | Token scopes and expiration, Bearer tokens | Signed and encrypted assertions |
| Complexity | Relatively simple, RESTful APIs | Complex, XML-based messaging |
| Mobile Friendliness | Highly suitable for mobile and API integrations | Less optimized for mobile environments |
| Session Management | Delegated access without session management | Supports full session management and logout |
| Use in Cloud | Widely used in modern APIs and cloud services | Common in enterprise federated identity systems |
Introduction to OAuth and SAML
OAuth is an open standard for access delegation commonly used to grant websites or applications limited access to user information without exposing passwords. SAML (Security Assertion Markup Language) is an XML-based framework designed for exchanging authentication and authorization data securely between parties, primarily used in enterprise single sign-on (SSO). Both protocols serve identity and access management purposes but differ in their approach, with OAuth focused on authorization and SAML emphasizing authentication.
Core Concepts: OAuth Explained
OAuth is an open-standard authorization protocol that enables applications to obtain limited access to user accounts on an HTTP service without exposing user credentials. It works through token exchange, where an access token represents the user's delegated permissions to access resources on a server. OAuth operates primarily as an authorization framework rather than an authentication protocol, facilitating secure third-party access while preserving user privacy and control.
Core Concepts: SAML Explained
SAML (Security Assertion Markup Language) is an XML-based framework designed for exchanging authentication and authorization data between security domains, primarily used in Single Sign-On (SSO) scenarios. It relies on assertions that contain statements about a user's identity and attributes, enabling trust between an Identity Provider (IdP) and a Service Provider (SP). Unlike OAuth, which focuses on delegated authorization, SAML specializes in providing secure, federated authentication through standardized protocols and message exchanges.
Protocol Workflows: How OAuth Works
OAuth operates through a series of defined protocol workflows, primarily involving resource owners, client applications, authorization servers, and resource servers. The typical OAuth flow begins with the client application requesting authorization from the resource owner, followed by the resource owner granting an authorization code, which the client exchanges with the authorization server for an access token. This access token then allows the client to access protected resources on the resource server without exposing user credentials, ensuring secure delegated access.
Protocol Workflows: How SAML Works
SAML (Security Assertion Markup Language) operates through a browser-based protocol where the identity provider (IdP) authenticates the user and sends an XML-based assertion to the service provider (SP) for access authorization. The process begins with the user requesting access to a service, which triggers a SAML authentication request to the IdP, resulting in a signed SAML assertion that confirms the user's identity and attributes. This assertion is validated by the SP, granting the user access to the requested resource without requiring direct credential exchange between the service and the user.
Use Cases: When to Use OAuth
OAuth is ideal for delegated access scenarios where users grant third-party applications limited permissions to their resources, such as social media login integrations and mobile app authentications. It excels in allowing secure API authorization without exposing user credentials, making it suitable for web, mobile, and desktop applications requiring user consent for data sharing. OAuth is preferred in modern cloud services and microservices architectures that demand scalable, token-based access management.
Use Cases: When to Use SAML
SAML is ideal for enterprise environments requiring single sign-on (SSO) across multiple internal systems or between organizations, especially in scenarios involving legacy applications and complex authentication flows. It excels in B2B federations and government or educational institutions where robust security and standardized identity assertions are mandatory. Implementing SAML is preferred when identity providers need to authenticate users for web-based applications using XML-based protocols in trusted domains.
Security Considerations: OAuth vs SAML
OAuth and SAML both provide secure authentication frameworks, but differ in their security models and use cases. OAuth primarily focuses on delegated authorization, enabling users to grant third-party applications limited access without sharing credentials, which requires careful management of access tokens to prevent interception or misuse. SAML, designed for enterprise single sign-on (SSO), uses XML-based assertions and typically employs strong encryption and digital signatures, offering robust identity verification but potentially facing risks from XML-based attacks if not properly configured.
Integration and Implementation Challenges
OAuth integration primarily targets authorization scenarios, offering token-based access control for APIs and mobile applications, which simplifies implementation but requires secure token management. SAML excels in enterprise single sign-on (SSO) environments, relying on XML-based assertions and complex SOAP messaging, often demanding extensive configuration with identity providers (IdPs) and service providers (SPs). Implementation challenges for OAuth include token expiration handling and scope management, while SAML faces difficulties in metadata exchange, certificate management, and compatibility with legacy systems.
Choosing the Right Protocol for Your Application
Choosing the right protocol between OAuth and SAML depends on your application's security needs and user experience goals. OAuth excels in delegated access scenarios, enabling third-party apps to access user resources without sharing credentials, making it ideal for mobile and web app integrations. SAML is best suited for enterprise single sign-on (SSO) solutions, providing robust authentication and authorization within federated identity environments, especially in legacy systems.
Identity Federation
OAuth enables secure delegated access for identity federation by authorizing third-party applications, while SAML provides standardized assertions for single sign-on (SSO) across enterprise domains.
Single Sign-On (SSO)
OAuth enables secure delegated access with token-based SSO, while SAML provides XML-based assertions for robust enterprise SSO authentication.
Access Token
OAuth issues access tokens to grant limited resource access, while SAML primarily uses assertions for authentication without directly providing access tokens.
Assertion
OAuth uses access tokens but does not rely on assertions, while SAML is assertion-based, exchanging XML assertions to authenticate and authorize users.
Authorization Grant
OAuth uses Authorization Grants such as Authorization Code, Implicit, Resource Owner Password Credentials, and Client Credentials to securely delegate access, while SAML primarily focuses on exchanging authentication and authorization assertions rather than using explicit grants.
Service Provider (SP)
OAuth enables Service Providers (SPs) to delegate authorization securely by granting limited access tokens, while SAML facilitates SPs in achieving single sign-on (SSO) through exchanging XML-based authentication assertions.
Identity Provider (IdP)
OAuth relies on Authorization Servers acting as Identity Providers to grant access tokens, whereas SAML uses dedicated Identity Providers to issue XML-based authentication assertions for secure single sign-on.
JSON Web Token (JWT)
OAuth primarily uses JSON Web Token (JWT) for secure, token-based authentication and authorization, whereas SAML relies on XML-based assertions for identity exchange.
Security Assertion Markup Language (SAML) Assertion
Security Assertion Markup Language (SAML) Assertion provides a robust, XML-based framework for exchanging authentication and authorization data securely between identity providers and service providers in single sign-on (SSO) implementations.
OpenID Connect (OIDC)
OpenID Connect (OIDC) enhances OAuth 2.0 by adding identity layer features for secure user authentication, whereas SAML serves primarily for enterprise single sign-on using XML-based assertions.
OAuth vs SAML Infographic
 njnir.com
njnir.com