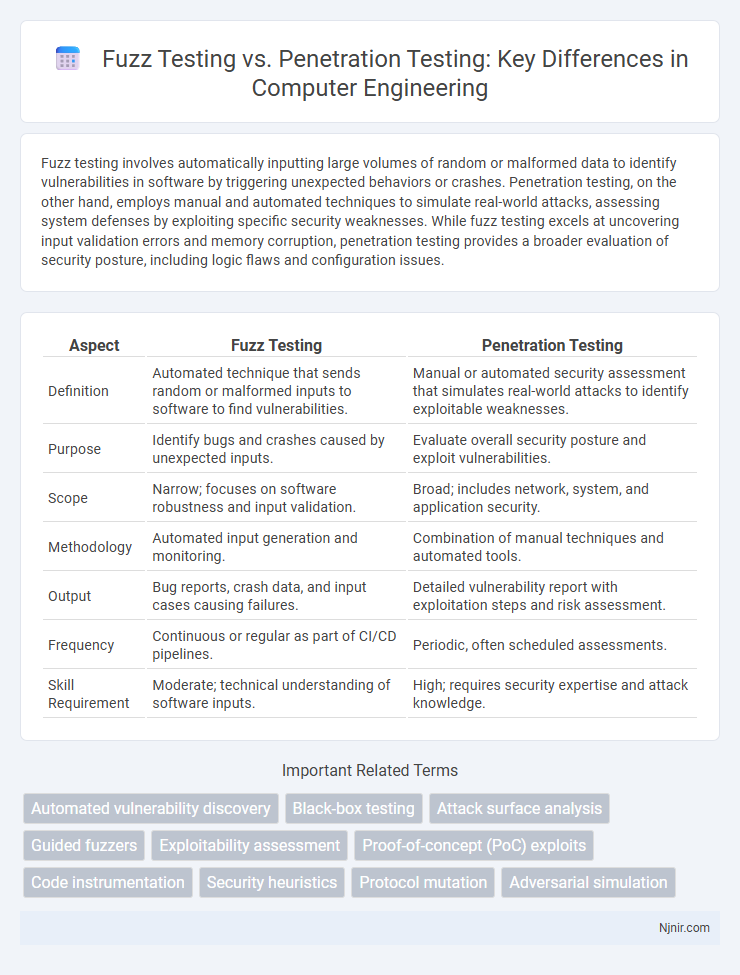
Fuzz testing involves automatically inputting large volumes of random or malformed data to identify vulnerabilities in software by triggering unexpected behaviors or crashes. Penetration testing, on the other hand, employs manual and automated techniques to simulate real-world attacks, assessing system defenses by exploiting specific security weaknesses. While fuzz testing excels at uncovering input validation errors and memory corruption, penetration testing provides a broader evaluation of security posture, including logic flaws and configuration issues.
Table of Comparison
| Aspect | Fuzz Testing | Penetration Testing |
|---|---|---|
| Definition | Automated technique that sends random or malformed inputs to software to find vulnerabilities. | Manual or automated security assessment that simulates real-world attacks to identify exploitable weaknesses. |
| Purpose | Identify bugs and crashes caused by unexpected inputs. | Evaluate overall security posture and exploit vulnerabilities. |
| Scope | Narrow; focuses on software robustness and input validation. | Broad; includes network, system, and application security. |
| Methodology | Automated input generation and monitoring. | Combination of manual techniques and automated tools. |
| Output | Bug reports, crash data, and input cases causing failures. | Detailed vulnerability report with exploitation steps and risk assessment. |
| Frequency | Continuous or regular as part of CI/CD pipelines. | Periodic, often scheduled assessments. |
| Skill Requirement | Moderate; technical understanding of software inputs. | High; requires security expertise and attack knowledge. |
Introduction to Security Testing in Computer Engineering
Fuzz testing automates the process of injecting malformed or unexpected inputs into software to identify vulnerabilities such as crashes and memory leaks, while penetration testing involves manual or automated simulated cyberattacks to uncover security weaknesses across systems. Both methods are essential components of security testing in computer engineering, complementing each other by exposing different types of threats--fuzz testing excels at finding input validation bugs, whereas penetration testing assesses broader attack vectors including logic flaws and configuration issues. Integrating fuzz testing with penetration testing enhances the robustness of security assessments by combining deep code-level analysis with real-world exploit scenarios.
Defining Fuzz Testing
Fuzz testing involves automatically inputting large volumes of random or unexpected data into software to identify security vulnerabilities and coding errors. This technique targets software robustness by triggering crashes, memory leaks, or faulty behavior through malformed inputs. Unlike penetration testing, which simulates real-world attacks, fuzz testing systematically uncovers hidden bugs by stress-testing input validation and error handling mechanisms.
Understanding Penetration Testing
Penetration testing involves simulating cyberattacks on systems to identify security vulnerabilities before malicious hackers can exploit them. It combines manual techniques and automated tools to assess the robustness of network defenses, application security, and system configurations. Unlike fuzz testing, which bombards inputs to trigger unexpected behavior, penetration testing provides a comprehensive analysis by mimicking real-world attack scenarios to evaluate overall security posture.
Key Differences: Fuzz Testing vs Penetration Testing
Fuzz testing systematically inputs invalid or random data into software to identify vulnerabilities such as memory leaks and crashes, prioritizing automation and breadth of coverage. Penetration testing involves manual, targeted attempts by security experts to exploit identified weaknesses, emphasizing depth of analysis and real-world attack scenarios. Fuzz testing excels in uncovering unknown bugs rapidly, while penetration testing provides comprehensive security assessments and remediation strategies.
Typical Use Cases for Fuzz Testing
Fuzz testing is primarily used to identify security vulnerabilities and stability issues by inputting random or malformed data into software applications, making it ideal for testing parsers, input validation modules, and network protocols. Typical use cases include uncovering memory corruption bugs, buffer overflows, and unexpected crashes in systems such as browsers, file formats, and communication services. Penetration testing, in contrast, focuses on simulating real-world cyberattacks to exploit weaknesses in overall system security, often involving manual methods and social engineering.
Common Applications of Penetration Testing
Penetration testing is commonly applied in network security assessments, web application security evaluations, and compliance audits to identify vulnerabilities before attackers exploit them. Organizations use pen testing to simulate real-world cyberattacks on systems such as firewalls, servers, and databases, ensuring robust defenses and regulatory compliance. Unlike fuzz testing, which primarily targets software bugs through randomized input, penetration testing provides comprehensive security analysis by combining manual and automated techniques.
Tools and Techniques: Fuzz Testing
Fuzz testing employs automated tools such as American Fuzzy Lop (AFL), libFuzzer, and Peach Fuzzer to generate large volumes of random or malformed inputs aimed at uncovering software vulnerabilities. Techniques involve input mutation, generation of unexpected data, and monitoring for crashes or memory leaks, enabling the detection of buffer overflows, assertion failures, and security loopholes. Unlike manual penetration testing, fuzz testing emphasizes systematic and continuous input bombardment to reveal hidden bugs effectively within codebases.
Tools and Techniques: Penetration Testing
Penetration testing employs tools such as Metasploit, Burp Suite, and Nmap to simulate real-world cyber attacks, identifying vulnerabilities in network infrastructure, web applications, and systems. Techniques include vulnerability scanning, exploitation, social engineering, and manual testing to assess security weaknesses comprehensively. Custom scripts and automated frameworks enable testers to exploit detected flaws, providing detailed reports for remediation strategies.
Complementary Roles in Secure Software Development
Fuzz testing and penetration testing serve complementary roles in secure software development by targeting different vulnerability aspects; fuzz testing automates input feeding to uncover unknown bugs and memory corruption issues, while penetration testing involves expert-driven attack simulations to identify exploitable security flaws. Combining fuzz testing's broad coverage of random inputs with penetration testing's strategic, goal-oriented assessments enhances detection of both common and complex vulnerabilities. Integrating both methods leads to a robust security posture by addressing software weaknesses from both automated anomaly detection and human-driven threat exploitation perspectives.
Choosing the Right Testing Approach for Your Project
Fuzz testing excels at identifying unknown vulnerabilities by inputting random or malformed data to uncover crashes and memory leaks, making it ideal for discovering low-level software bugs. Penetration testing provides a human-led, targeted approach to simulate real-world cyberattacks, focusing on business logic flaws and security weaknesses within an application's environment. Selecting between fuzz and penetration testing depends on project goals, with fuzz testing suited for early-stage development and automated vulnerability discovery, while penetration testing is recommended for assessing systemic security risks and compliance in deployed systems.
Automated vulnerability discovery
Fuzz testing automates vulnerability discovery by inputting random or malformed data to identify security flaws, while penetration testing involves manual or automated techniques to simulate real-world attacks for comprehensive security assessment.
Black-box testing
Fuzz testing, a black-box technique injecting malformed inputs to discover software vulnerabilities, contrasts with black-box penetration testing that simulates real-world attacks to identify security weaknesses without internal code knowledge.
Attack surface analysis
Fuzz testing systematically identifies vulnerabilities by injecting malformed inputs into software, expanding attack surface analysis, while penetration testing simulates real-world attacks to evaluate security posture by targeting known and potential entry points.
Guided fuzzers
Guided fuzzers enhance fuzz testing by using feedback-driven algorithms to systematically explore vulnerabilities, offering more precise and efficient identification of security flaws compared to traditional penetration testing methods.
Exploitability assessment
Fuzz testing automates input mutation to identify software vulnerabilities by triggering crashes, while penetration testing manually exploits known weaknesses to assess real-world exploitability and security impact.
Proof-of-concept (PoC) exploits
Fuzz testing generates automated inputs to discover software vulnerabilities for PoC exploits, while penetration testing uses manual and automated methods to identify security weaknesses and produce PoC exploits demonstrating real-world attack scenarios.
Code instrumentation
Fuzz testing leverages automated code instrumentation to inject malformed inputs and monitor software behavior for vulnerabilities, whereas penetration testing primarily relies on manual techniques without deep code instrumentation.
Security heuristics
Fuzz testing automates input anomalies detection to expose software vulnerabilities, while penetration testing uses human-driven tactics and heuristics to identify security flaws through controlled attacks.
Protocol mutation
Fuzz testing uses automated protocol mutation to identify vulnerabilities by sending malformed data, while penetration testing relies on manual techniques to exploit protocol weaknesses.
Adversarial simulation
Fuzz testing leverages automated input generation to identify software vulnerabilities, while penetration testing employs targeted adversarial simulation to mimic real-world cyberattacks and assess system defenses.
Fuzz testing vs Penetration testing Infographic
 njnir.com
njnir.com